Healthcare is Having a Digital Identity Crisis
Why modern healthcare needs consumer identity and access management.

Healthcare today is having a patient identity crisis. Patients juggle multiple logins across health portals and struggle to share their records with the right people. A casual browsing session can mistakenly link to someone else's profile, and a shared email address or device can easily damage patient data. These aren’t just minor hiccups—they can lead to serious privacy breaches, patient safety issues, and a poor experience.
For those guiding healthcare organizations, it’s crucial to move beyond ad hoc, “make do” identity practices. Digital identity must be robust and address the unique challenges of healthcare. I've been in the weeds on the current state of identity in healthcare for the past three years through my work with Providence, Praia Health, and activities with the CARIN Alliance, and this post collects what I've realized through my work.

Healthcare Identity is Insecure
The present state of identity has led to systemic security issues with our healthcare systems and delivery. Some of the most personal and private data about you is sitting behind minimal protections, and this has created a ticking time bomb, both of liability for healthcare services and exposure for your data.
The Danger of Indirect Identity
Because few health systems have adopted an identity standard like Identity Assurance Level 2 (IAL2) at every data storage or retrieval point, they're left establishing patient identity using indirect methods. Attributes that taken together should, roughly, equate to a singular person. This approach hasn't changed materially in the last two decades. This approach causes a significant risk of profile corruption and of improper access.
Because this has been the approach for so long, it's hard to understand why it's deeply flawed and causing risk to your data right now. So, let me break down the reasons an indirect identity is flawed:
People Can't Reliably Provide Their Details
Asking anyone to provide their own email, phone number, and address creates fertile ground for invalid data. I'm not beyond mistyping my data in a hurry. When entered, contact details are also subject to data entry errors. When user-provided, human-entered information goes directly into a source-of-truth system (like an EMR) or a data lake that will be a source of personalization, you're introducing substantial risk.
Phone Numbers Alone Aren't Identity
Phone numbers, and especially cell phone numbers, are increasingly being using inside healthcare as an identity proxy, even as other industries are moving away from SMS as insecure. Even if you prove a phone number belongs to a single person, you only establish that link at a specific moment.
It is shockingly easy to hijack a phone number for a targeted victim; and therefore SMS-based consumer engagement tools that can act on behalf of the patient. Using SMS as your primary MFA method for consumers is risky for the same reason.
I recently called a provider (I won't call them out directly here) and could authenticate with their IVR using only my phone number and zip code. This is mind-blowingly insecure!
Email Addresses aren't Identity
I’ve had my email for a long time and ended up with a short, desirable address. The downside? I get other people's emails constantly. Five other Robin's have given my address out as theirs to utility companies, tax authorities, and healthcare providers in the last two months. I've even reached out before letting some companies know they had the wrong email address, but it happens with such consistency I've just started trashing the emails instead.
It’s common to use email as a username or unique ID for patients. After all, “everyone has an email address,” so what’s the harm? The harm is that emails are not actually unique or permanent identifiers. People share email accounts (think of spouses or siblings using a family email) and people change or lose access to their email. This is assuming they even give the right address to begin with.
If a user can reset their password just by sending a code to their email, your system is insecure. Email is just a contact point, not a proof of personhood. In short, an email might look like a handy identifier, but it’s as unsafe as using a phone number.
What About Combinations?
I've heard people make this suggestion. We won't just validate people based on email. We'll use a combination of information. Surely requiring email and phone and full name and the last four SSN digits will work. Maybe asking consumer credit report knowledge questions too, that'll fix it, right?
No. No, it won't. In fact, it's arguably worse, as it gives a false sense of security while also making accessing records harder for legitimate reasons.
Thanks to massive breaches like the Equifax hack in 2017, a trove of personal data (Social Security numbers, past addresses, loans, etc.) is out in the wild. Attackers can often scrape together enough info to pass knowledge-based quizzes on identity verification. Questions like “Which of these addresses have you lived at?” or “What was your mortgage payment in 2010?” may now be easier for an attacker to answer than the legitimate person.
Knowledge-based verification (KBV) or knowledge-based authentication SHALL NOT be used for identity verification. (emphasis theirs)
NIST SP 800-63A 2.5.1
Recognizing this, NIST explicitly withdrew its support for knowledge-based authentication (KBA) and knowledge-based verification (KBV) in its digital identity guidelines.
These methods also frustrate legitimate users as credit bureau identity checks suffer from data quality issues. Studies have shown a significant fraction of credit reports contain errors or even mixed information from different people. In fact, the CFPB reported that about 42% of credit reporting complaints in 2023 were about incorrect information on a credit report. I, for a time, had a previous landlord's past addresses on my profile and had to memorize and enter them to pass KBV checks.
Consumers stated that CRAs incorrectly reported account balances, account opening dates, payment dates, bankruptcies, payment statuses, inquiries, and personal information. Some consumers stated their reports contained tradelines that they were unfamiliar with or bankruptcies they never filed.
CFPB Consumer Response Annual Report, 2023
Using knowledge questions as identity proxies can lead to false positives (approving the wrong person) or false negatives (failing to recognize the right person) and allow attackers to impersonate a target. Healthcare organizations should treat those methods as supplementary at best (for instance, to reach Identity Assurance Level 2 by verifying documents), and always with more robust verification steps. The industry trend, following NIST guidance, is toward strong identity proofing (e.g. government IDs, biometrics) for critical access, and away from easily stolen personal trivia.
Indirect Identity Evaluation
If you work for a health system (or anywhere you have to control access to sensitive records), ask yourself what a bad (or even confused) actor could do if their email or phone number were on a patient record?
From experience, I've seen EMRs configured to send check-in and appointment information directly to the email on file, and clicking on the links in those emails immediately logs you into that patient account without a password. This is effectively a zero-factor authentication.
What could a bad actor do if they gained access to a patient's phone number or texts? What tools you are using assume an identity based only on phone number possession? Are there any services you use that communicate with a patient directly over texting without additional identity verification?
The Danger of Identity Mixing
Intentional Profile Sharing
Historically, research has found it difficult to get proxy access for caregivers. What do these caregivers do then? They just logged in as the patient, using the patient’s credentials. This sharing is understandable in context, but it completely breaks securing access to a single personal identity–the system thinks it’s always the patient, and does not know when it’s the daughter or spouse accessing on their behalf.
The risks are significant: privacy violations (sensitive results the patient might not want to share), or even medical errors if clinicians assume they’re communicating with the patient when it’s really someone else. Health systems must configure their EMRs to allow proxy access, ensure their authentication systems account for this access, and make requesting and disabling proxy access secure and easy.
Incorrect Record Merging
Misused identity markers can also lead to nightmare scenarios. Sacred Heart accidentally merged the records of two women with similar names. The family's first sign that something was wrong was a phone call telling them their family member was in the ER. Actually, she was with them! The woman found someone else's medical information in her online chart and had even received a hospital bill for nearly $3,000 for services she never received.
When two similar people are in a source-of-truth system, without having foundational identities verified, providers depend on patient matching based on: what the patient shares, what the attending staff search for and enter, and an administrators's best judgement on if two records are the same person.
A proper account system alone can’t solve human errors in data entry, but it can mitigate them by using more robust unique identifiers and requiring verified identification at account creation. For instance, if each patient had a verified digital identity (say verified via phone and ID document), the chance of two distinct individuals being conflated drops dramatically.

The Current State of Identity Is Failing Patients
Confused Personal Information
When anyone first visits a healthcare site or app without logging in, they operate under a transient identity; an anonymous or temporary identifier (like a cookie or device ID) that says “this is a unique visitor” but not who they are. Conversely, a verified user account anchors an authenticated identity (e.g., a logged-in patient or someone who has proven their identity).
The transient approach is useful for personalization and tracking, but it can be dangerously misleading if treated with the same confidence as a confirmed identity. You'll often hear this marketed as a "360 degree view". Tag management and analytics systems that assign a unique cookie ID to each device to track site activity. When that device’s user eventually logs in, the system may link all prior “anonymous” activity to the now-known user. On a single-user device, that may be OK, but on shared devices or with mixed-use scenarios, it can spell trouble.
You can experience this right now. Open a private browsing session and go to the Aetna website, and look at their home page. Notice how in the top-right there's a member login link for employer and marketplace plans. Now, open another private window and go to Aetna's medicare support page (which, at least for me is the second result on Google for "Aetna email address"), then in the same private browsing session try to go to Aetna.com again. You can't! Aetna redirects you to a Medicare and Medicare Advantage flow, eliminating the non-Medicare login option. A pretty frustrating experience for a consumer.
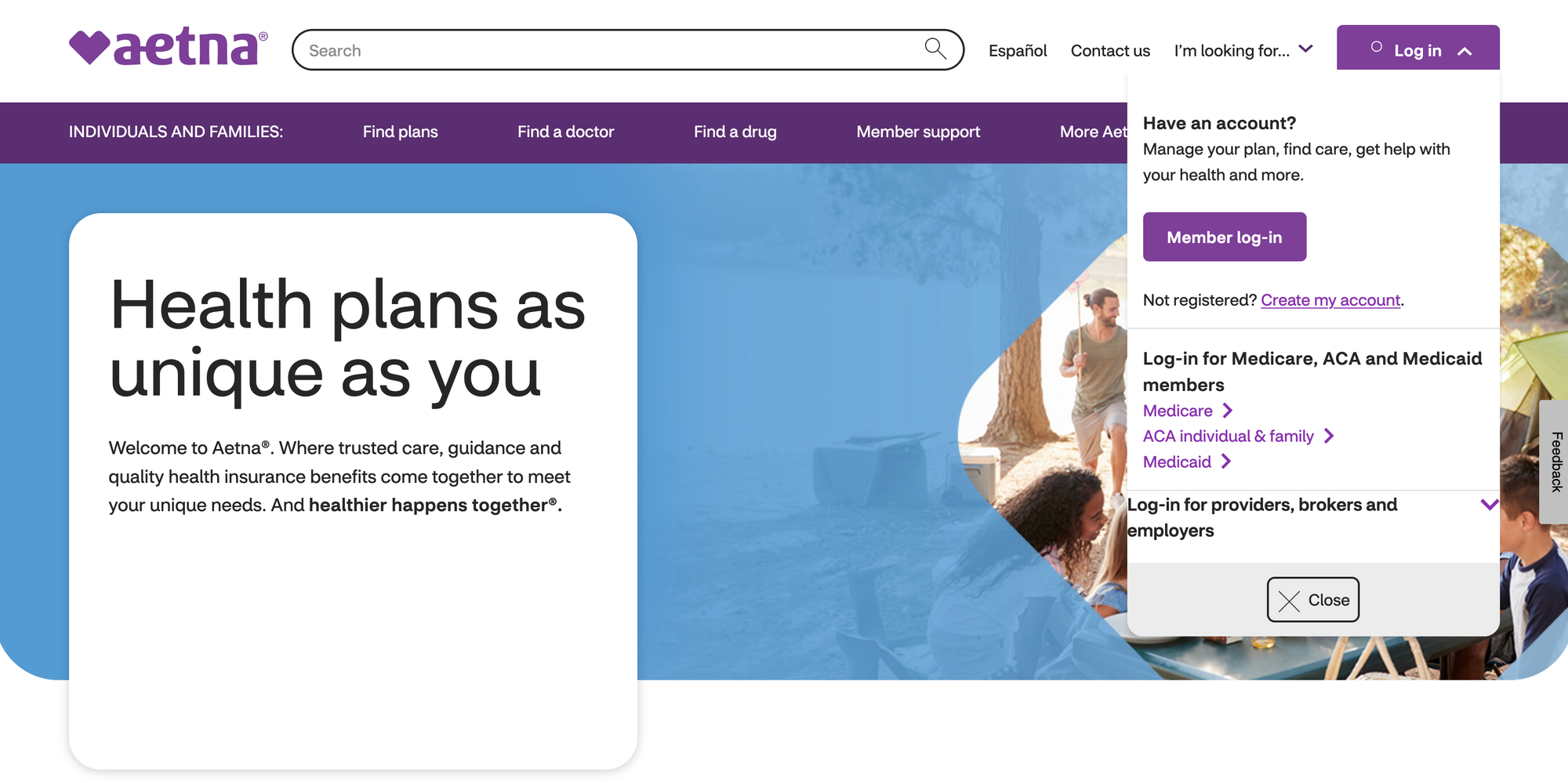
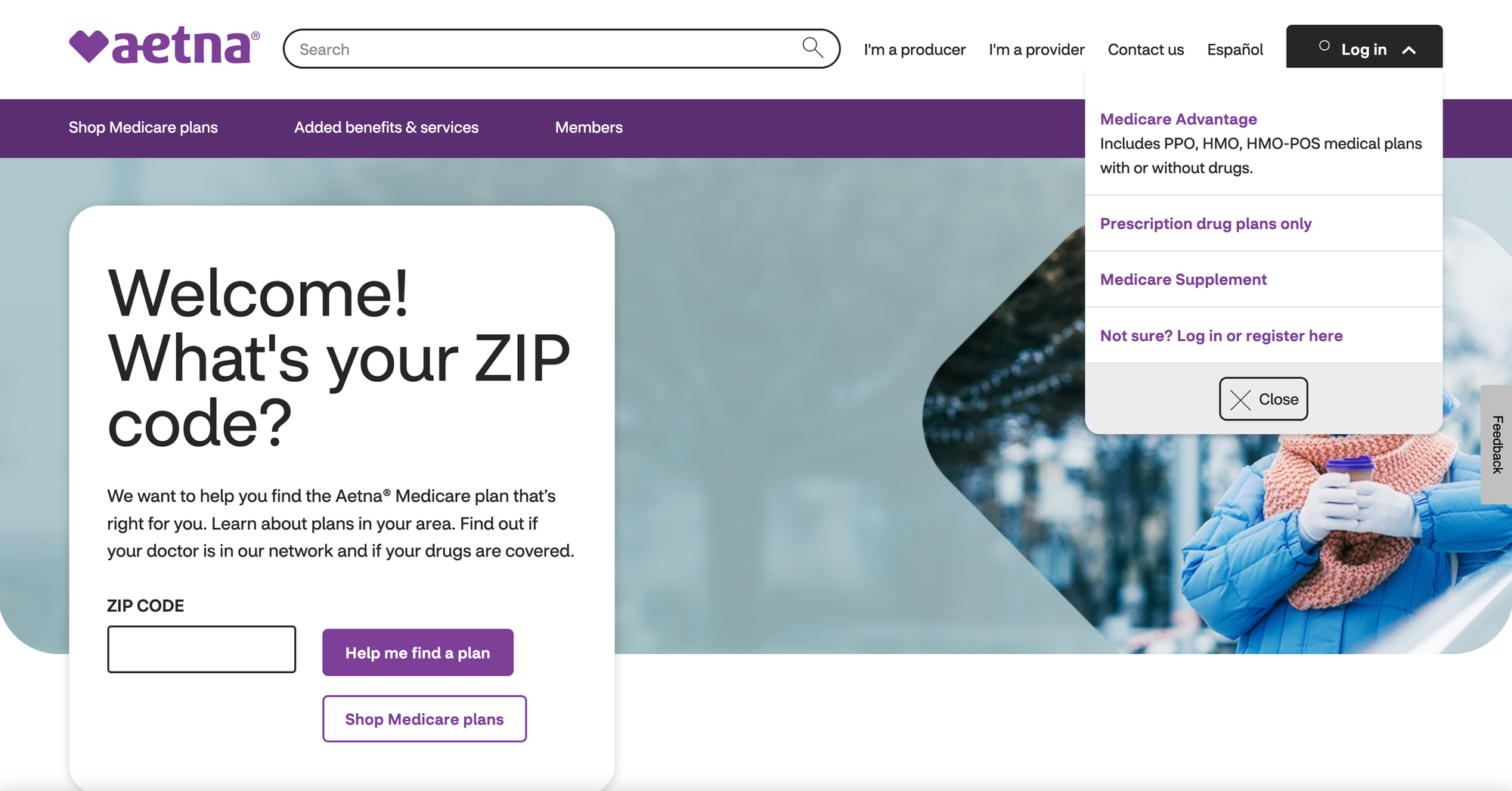
For another example, if a husband and wife share the same desktop or same iPad; the wife's transient identity suggests she's a woman in her 40s, interested in diet advice, and reading articles about diabetes. If her husband subsequently uses the same device and creates an account, the personalization system might mistakenly add these inferred attributes to his profile. Improper tracking of the source of these assumptions could lead to at least poor targeting and, at worst, actual harm. Transient identifiers (like device fingerprints or cookies), when given equal weight and mixed with multiple sources in a data lake, cause this profile mixing.
Fingerprinting, often sold as a robust solution for identity resolution, isn’t up to the task. It’s decent for demographic personalization, but beyond that, it’s dangerous. Fingerprinting technologies are greedy: they accept inconsistent data, showing confidence metrics that do not identify anyone. Worse, they’re naïve, designed for probabilistic personalization, not security. This opens the door to exploits like replay attacks, session spoofing, and engineered sessions. Fingerprinting can be a useful supplement for security (like detecting fraud or concurrent logins), but it’s not a substitute for a verified identity.
Account Recovery and Duplication
We’ve seen patients who forget login info and end up making a second account with a different email; now they have two partial identities in the system. Each account might each have bits of their records. A consumer identity system that guides a patient through identity verification both creates a more certain initial record for that patient and provides robust account recovery (self-service password reset, username reminder).
A well-configured consumer identity system can also detect duplicate registrations and guide them securely into a logged in state. By reducing duplicate accounts, consumer identity helps maintain one identity per verified individual, which is the holy grail for accurate records.
Inconsistent Experience
I touched on this above when mentioning Single Sign-On (SSO) as a benefit of implementing consumer identity properly. But it also goes beyond just letting a consumer use the same credentials for multiple tools. A strong organizational tie to consumer identity (as seen with Google accounts and their widespread "Sign In With Google" buttons) generates an additional brand signal. It also reduces friction when completing user journeys across multiple tools, as the same session continues.
When you're reading Google News to start your morning, then switch over to Gmail and see a flight deal from Kayak, then go to Kayak and sign in with Google to buy that flight. You're not needing to go through a full login flow with each tool. At most, you logged in when you first went to Google News, and after that you never needed to enter a username and password again. Two of those were separate web applications operated by Google, and the third was a totally independent company that offers the login option as a convenience for their shared customers. All of this is done securely with consumer identity standards.
Personalization is great, but we must build it on a foundation of accurate identity. A “customer 360” that accidentally combines two people is worse than having no 360-degree view at all. Ensuring clear separation of profiles and using identity verification before merging data streams is essential. It’s here that Consumer Identity and Access Management (CIAM) systems can help by providing a unified, stable identifier that all analytics and personalization tools can reference, rather than each tool doing fuzzy matching on its own. When each patient has one login and one identity across all digital touchpoints, the temptation to do probabilistic guessing diminishes–and so does the risk of humiliating or dangerous personalization mistakes.

The Promise of Healthcare CIAM
Better Security and Happier Patients
Having a secure patient identity helps with consumer conversion, gives a better patient experience, avoids incorrect billing, and helps stop leakage by making it easy for a patient to complete their medical journey with a single provider. Implementing a consumer identity also improves security at the protocol level, at the storage level, and at the consumer level.
Unified, Accurate Identity Across All Platforms
A Consumer Identity and Access Management (CIAM) system designed for healthcare provides a single source of truth for patient identity. Instead of each application creating its own login and siloed user info, patients get a single account that links to all services. This drastically reduces the chance of duplicate or mismatched identities.
If John Doe has one profile, all his interactions (portal visits, mobile app logins, telemedicine appointments) tie back to that one profile. The platform handles linking accounts (even allowing social logins or federated logins to be mapped into the same user record). Modularity is a key benefit here. Health IT teams can plug new apps or data sources into the CIAM via standard protocols, and immediately those apps are part of the unified login experience. Thanks to federation, that account can also extend to lab and imaging providers and partner apps as well.
Not have a consistent account experience with SSO encourages users to choose weak passwords and practice poor session hygiene. With a central CIAM tool when a hospital system rolls out a new wellness coaching app, they don’t need to create new usernames and passwords; they can rely on the existing patient login. This speeds up deployment and reduces the number of login points; it also prevents IT and call center operations from being burdened by multiple identity stores.
Better Patient Experience and Engagement
One of the most visible benefits of CIAM is a smoother experience for patients, which drives adoption of digital tools. With a dedicated CIAM, we can implement single sign-on (SSO) for patients across multiple services. For example, a patient logs into the hospital’s main portal and from there can jump to billing, lab results, a virtual visit platform, and a pharmacy refill system without signing in again each time. Those systems trust the central identity.
This is analogous to how an employee can access multiple work applications after a onetime login to the company SSO, but now it’s the patient enjoying that convenience. CIAM also allows progressive profiling, letting someone book a vaccine appointment with just a phone number verification, but then encouraging them to create a full account later to see results. This lowers the barrier to entry for new users. All these ease-of-use improvements lead to higher portal usage and patient engagement.
Patients are more likely to use and trust a system that remembers them and spares them repetitive identity proof steps. And engaged patients have better outcomes and satisfaction. In fact, a strong identity layer is foundational to “digital front door” strategies that many healthcare organizations pursue.
Personalization and Modular Innovation
With a robust CIAM, healthcare providers can more confidently personalize services without fearing the profile mix-ups described earlier. Because the system clearly delineates and authenticates each user's identity, personalization engines use reliable account data instead of guesswork.
For example, a CIAM might maintain links between family member accounts (with proper consent), so that an app knows who is the parent and who is the child in a pediatric portal scenario, eliminating confusion when tailoring content. Also, CIAM’s data integrations can feed into analytics: by consolidating a patient’s interactions, the organization can drive insights into their needs (with consent) and offer targeted interventions.
This is essentially creating a holistic patient profile safely and even allow creations of a digital patient double, which is a comprehensive digital profile of a patient across all interactions. That can power AI-driven health insights and proactive care. Without a solid identity backbone, such efforts often fail or pose too much risk.
CIAM lends modularity to the overall architecture: want to swap in a new telehealth vendor? As long as they support standard federated login, they can slot into your CIAM and patients won’t need new accounts. Want to collaborate with a partner (B2B) or allow an external app (via API) to access patient data with patient consent? A good CIAM (like the one built into the Praia Health platform) can handle issuing tokens with the right scopes, logging the consents, and offloading that complexity from your application layer.
A hospital might modernize its digital front door by assembling best-of-breed apps (appointment scheduling from Vendor A, virtual visits from Vendor B, health record access from the EHR vendor, etc.). Without a CIAM, each of those require separate logins or clunky custom integration. With one, the patient logs in once and gets a unified experience across all services. The system handles authentication centrally and issues tokens to each app to allow access.
This modular, API-driven approach is key to avoiding the tech debt of monolithic systems. You can modernize components one at a time, or even change and merge EMRs, while the identity layer remains consistent. Your identity manager becomes an identity hub for your digital health ecosystem, allowing various modules (EHR, CRM, patient apps, wearables, etc.) to inter-operate via a common identity standard.
Support for Standards and Interoperability
Healthcare can only be a sustainable business through interoperability. CIAM can facilitate this by serving as the authentication and authorization gateway for external data requests. For instance, when a third-party app wants to connect to your system via a FHIR API on behalf of a patient, an OAuth 2.0/OIDC-compliant CIAM can handle that by obtaining patient consent and issuing an access token (this is the essence of “SMART on FHIR” and similar standards in digital health). Many EMRs offer user management today, but lack the ability to make that a truly portable identity that supports open standards and full SSO.
By using well-established standards (OAuth 2.0, OIDC, and SAML for legacy systems), a CIAM ensures that your healthcare org isn’t locking itself into proprietary or brittle methods. It can also inter-operate with national or regional digital identity initiatives (such as login.gov for veterans). All of this reduces the custom work your team has to do and increases trust, as patients can use identities they already trust to access your services.
CIAM also helps enforce least-privilege access via proper authorization scopes. For example, an integrated system can ensure that when a patient grants a third-party wellness app access to their health data, it’s limited to the consent given for the duration needed while having a central place for that access to be revoked.
It’s a win-win-win: patients get convenience, providers get accuracy and safety, and the organization can introduce new digital offerings faster with less risk.

Conclusion
It's Time to Solve the Identity Crisis
Digital identity might not be as headline-grabbing as the latest medical AI or surgical robot, but it's make-or-break foundation for digital health initiatives that can easily double or triple implementation time frames for every new imitative if not solved foundationally.
A seamless yet secure patient experience, the integrity of health data, and even patient safety now hinge on getting identity management right. We can't afford to treat patient identity as a casual add-on. The examples we’ve explored, from wrong records to merged profiles and security gaps, illustrate that the costs of weak identity practices are very real: privacy breaches, regulatory penalties, frustrated patients, misinformed clinicians, and reputational damage.
On the flip side, investing in a robust, healthcare-focused Consumer Identity and Access Management solution offers a path to not only avoid those pitfalls but actively improve healthcare delivery. With CIAM in place, a health system can confidently answer questions like: “Is this digital service really reaching the right patient?”, “Can our patients easily access all their health services without remembering five logins?”, “Are we sure only allowed individuals are seeing this sensitive data?”, and “How quickly can we plug in this new app into our ecosystem?” Having a firm identity foundation can let you answer those questions with certainty.
A reliable digital identity framework builds trust, arguably the most important currency in healthcare. Patients will trust that their information is secure and accurate, clinicians will trust that the patients can access tools easily, and executives will trust that their digital investments are actually reaching and benefiting the intended population.
I, of course, work at Praia Health and think the platform is pretty awesome. But I'm also happy to talk with anyone working in a health system and struggling to find the right answer for patient identity, because having open discussions about patient identity helps us all. You'll end up with the worst compromise if you wait for a vendor who doesn't specialize in CIAM to add it, or for regulation to require it. You can reach out to me here and I'll be happy to get in touch.
